Main Article Content
Abstract
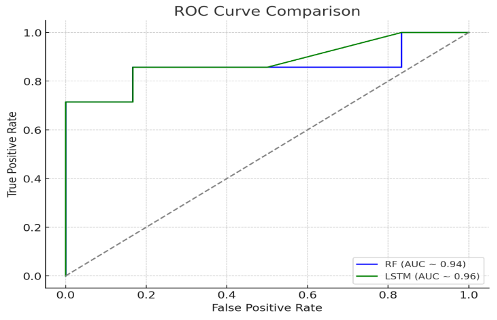
The growing integration of Internet of Things (IoT) devices in healthcare has revolutionized patient care and operational efficiency. However, this advancement comes with vast cybersecurity demanding situations, as IoT devices are exceedingly susceptible to diverse cyber-attacks, which include statistics breaches, denial-of-provider (DoS) attacks, and unauthorized get right of entry to. This look at proposes a robust cyber-assault detection machine through leveraging Random Forest (RF) and Long Short-Term Memory (LSTM) algorithms, which integrate static sample popularity with sequential facts analysis. RF is utilized for its performance in coping with dependent statistics, along with network visitors and tool logs, at the same time as LSTM excels in analyzing time-collection facts, allowing the detection of evolving threats. The proposed hybrid RF-LSTM version became evaluated using real-global IoT healthcare datasets. RF established high accuracy in detecting static anomalies, accomplishing an accuracy of ninety four% and a precision of ninety three%. LSTM excelled in coping with temporal dependencies, reaching an F1 score of 91% and minimizing fake negatives. The integration of both algorithms more desirable the gadget's capability to stumble on a huge variety of attacks, reaching an common detection accuracy of ninety seven% in real-time scenarios. This research highlights the capability of hybrid fashions in ensuring IoT safety and mitigating cyber threats in healthcare environments, making sure patient protection and information integrity.
Keywords
Article Details
Copyright (c) 2024 Atheer Alaa Hammad (Author)

This work is licensed under a Creative Commons Attribution 4.0 International License.
How to Cite
References
- H. HaddadPajouh, A. Dehghantanha, R. M. Parizi, M. Aledhari, and H. Karimipour, "A survey on internet of things security: Requirements, challenges, and solutions," Internet of Things, vol. 14, p. 100129, 2021, doi: https://doi.org/10.1016/j.iot.2019.100129
- A. Boukerche and R. Coutinho, "Design Guidelines for Machine Learning-based Cybersecurity in Internet of Things," IEEE Network, vol. 35, pp. 393-399, 2020, doi: http://dx.doi.org/10.1109/MNET.011.2000396
- F. Wu, C. Qiu, T. Wu, and M. R. Yuce, "Edge-based hybrid system implementation for long-range safety and healthcare IoT applications," IEEE Internet of Things Journal, vol. 8, no. 12, pp. 9970-9980, 2021, doi: https://doi.org/10.1109/JIOT.2021.3050445
- M. Waqas et al., "Botnet attack detection in Internet of Things devices over cloud environment via machine learning," Concurrency and Computation: Practice and Experience, vol. 34, no. 4, p. e6662, 2022, doi: https://doi.org/10.1002/cpe.6662
- K. Prathapchandran and T. Janani, "A trust aware security mechanism to detect sinkhole attack in RPL-based IoT environment using random forest–RFTRUST," Computer Networks, vol. 198, p. 108413, 2021, doi: https://doi.org/10.1016/j.comnet.2021.108413
- X. Wang, T. Liu, C. Feng, D. Fang, and X. Chen, "RF-CM: Cross-modal framework for rf-enabled few-shot human activity recognition," Proceedings of the ACM on Interactive, Mobile, Wearable and Ubiquitous Technologies, vol. 7, no. 1, pp. 1-28, 2023, doi: https://doi.org/10.1145/3580859
- Y. Zhang et al., "Efficient and intelligent attack detection in software defined IoT networks," in 2020 IEEE International Conference on Embedded Software and Systems (ICESS), Shanghai, China, 2020: IEEE, pp. 1-9, doi: https://doi.org/10.1109/ICESS49830.2020.9301591
- S. Djaballah, L. Saidi, K. Meftah, A. Hechifa, M. Bajaj, and I. Zaitsev, "A hybrid LSTM random forest model with grey wolf optimization for enhanced detection of multiple bearing faults," Scientific Reports, vol. 14, p. 23997, 2024, doi: https://doi.org/10.1038/s41598-024-75174-x
- C. U. Om Kumar, J. Durairaj, S. A. Ahamed Ali, Y. Justindhas, and S. Marappan, "Effective intrusion detection system for IoT using optimized capsule auto encoder model," Concurrency and Computation: Practice and Experience, vol. 34, no. 13, p. e6918, 2022, doi: https://doi.org/10.1002/cpe.6918
- W. Li, S. Vishwakarma, C. Tang, K. Woodbridge, R. J. Piechocki, and K. Chetty, "Using RF transmissions from IoT devices for occupancy detection and activity recognition," IEEE Sensors Journal, vol. 22, no. 3, pp. 2484-2495, 2021, doi: https://doi.org/10.1109/JSEN.2021.3134895
- A. K. Kalusivalingam, A. Sharma, N. Patel, and V. Singh, "Employing Random Forests and Long Short-Term Memory Networks for Enhanced Predictive Modeling of Disease Progression," International Journal of AI and ML, vol. 2, no. 3, 2021
- B. Barnes-Cook and T. O'Shea, "Scalable wireless anomaly detection with generative-LSTMs on RF post-detection metadata," in 2022 IEEE Wireless Communications and Networking Conference (WCNC), Austin, TX, USA, 2022: IEEE, pp. 483-488, doi: https://doi.org/10.1109/WCNC51071.2022.9771754
- N. Varshney, P. Madan, A. Shrivastava, A. P. Srivastava, C. P. KUMAR, and K. Khan, "Real-Time Anomaly Detection in IoT Healthcare Devices With LSTM," in 2023 International Conference on Artificial Intelligence for Innovations in Healthcare Industries (ICAIIHI), Raipur, India, 2023, vol. 1: IEEE, pp. 1-6, doi: https://doi.org/10.1109/ICAIIHI57871.2023.10489823
- I. A. Kandhro et al., "Detection of real-time malicious intrusions and attacks in IoT empowered cybersecurity infrastructures," IEEE Access, vol. 11, pp. 9136-9148, 2023, doi: https://doi.org/10.1109/ACCESS.2023.3238664
- F. Sattari, A. H. Farooqi, Z. Qadir, B. Raza, H. Nazari, and M. Almutiry, "A hybrid deep learning approach for bottleneck detection in IoT," IEEE Access, vol. 10, pp. 77039-77053, 2022, doi: https://doi.org/10.1109/ACCESS.2022.3188635
- M. K. Saeed, A. Al Mazroa, B. M. Alghamdi, F. S. Alallah, A. Alshareef, and A. Mahmud, "Predictive analytics of complex healthcare systems using deep learning based disease diagnosis model," Scientific Reports, vol. 14, p. 27497, 2024, doi: https://doi.org/10.1038/s41598-024-78015-z
- M. Al Razib, D. Javeed, M. T. Khan, R. Alkanhel, and M. S. A. Muthanna, "Cyber threats detection in smart environments using SDN-enabled DNN-LSTM hybrid framework," IEEE Access, vol. 10, pp. 53015-53026, 2022, doi: https://doi.org/10.1109/ACCESS.2022.3172304
- N. Sun et al., "Cyber threat intelligence mining for proactive cybersecurity defense: a survey and new perspectives," IEEE Communications Surveys & Tutorials, vol. 25, no. 3, pp. 1748-1774, 2023, doi: https://doi.org/10.1109/COMST.2023.3273282
- S. Ali, S. U. Rehman, A. Imran, G. Adeem, Z. Iqbal, and K.-I. Kim, "Comparative evaluation of ai-based techniques for zero-day attacks detection," Electronics, vol. 11, no. 23, p. 3934, 2022, doi: https://doi.org/10.3390/electronics11233934
- W. Ding and H. Sun, "Prediction of PM2. 5 concentration based on the weighted RF-LSTM model," Earth Science Informatics, vol. 16, pp. 3023-3037, 2023, doi: https://doi.org/10.1007/s12145-023-01111-7
- M. Almehdhar et al., "Deep learning in the fast lane: A survey on advanced intrusion detection systems for intelligent vehicle networks," IEEE Open Journal of Vehicular Technology, vol. 5, pp. 869-906, 2024, doi: https://doi.org/10.1109/OJVT.2024.3422253
- F. Zahra, N. Jhanjhi, N. Khan, S. N. Brohi, M. Masud, and S. Aljahdali, "Protocol-specific and sensor network-inherited attack detection in IoT using machine learning," Applied Sciences, vol. 12, no. 22, p. 11598, 2022, doi: https://doi.org/10.3390/app122211598
References
H. HaddadPajouh, A. Dehghantanha, R. M. Parizi, M. Aledhari, and H. Karimipour, "A survey on internet of things security: Requirements, challenges, and solutions," Internet of Things, vol. 14, p. 100129, 2021, doi: https://doi.org/10.1016/j.iot.2019.100129
A. Boukerche and R. Coutinho, "Design Guidelines for Machine Learning-based Cybersecurity in Internet of Things," IEEE Network, vol. 35, pp. 393-399, 2020, doi: http://dx.doi.org/10.1109/MNET.011.2000396
F. Wu, C. Qiu, T. Wu, and M. R. Yuce, "Edge-based hybrid system implementation for long-range safety and healthcare IoT applications," IEEE Internet of Things Journal, vol. 8, no. 12, pp. 9970-9980, 2021, doi: https://doi.org/10.1109/JIOT.2021.3050445
M. Waqas et al., "Botnet attack detection in Internet of Things devices over cloud environment via machine learning," Concurrency and Computation: Practice and Experience, vol. 34, no. 4, p. e6662, 2022, doi: https://doi.org/10.1002/cpe.6662
K. Prathapchandran and T. Janani, "A trust aware security mechanism to detect sinkhole attack in RPL-based IoT environment using random forest–RFTRUST," Computer Networks, vol. 198, p. 108413, 2021, doi: https://doi.org/10.1016/j.comnet.2021.108413
X. Wang, T. Liu, C. Feng, D. Fang, and X. Chen, "RF-CM: Cross-modal framework for rf-enabled few-shot human activity recognition," Proceedings of the ACM on Interactive, Mobile, Wearable and Ubiquitous Technologies, vol. 7, no. 1, pp. 1-28, 2023, doi: https://doi.org/10.1145/3580859
Y. Zhang et al., "Efficient and intelligent attack detection in software defined IoT networks," in 2020 IEEE International Conference on Embedded Software and Systems (ICESS), Shanghai, China, 2020: IEEE, pp. 1-9, doi: https://doi.org/10.1109/ICESS49830.2020.9301591
S. Djaballah, L. Saidi, K. Meftah, A. Hechifa, M. Bajaj, and I. Zaitsev, "A hybrid LSTM random forest model with grey wolf optimization for enhanced detection of multiple bearing faults," Scientific Reports, vol. 14, p. 23997, 2024, doi: https://doi.org/10.1038/s41598-024-75174-x
C. U. Om Kumar, J. Durairaj, S. A. Ahamed Ali, Y. Justindhas, and S. Marappan, "Effective intrusion detection system for IoT using optimized capsule auto encoder model," Concurrency and Computation: Practice and Experience, vol. 34, no. 13, p. e6918, 2022, doi: https://doi.org/10.1002/cpe.6918
W. Li, S. Vishwakarma, C. Tang, K. Woodbridge, R. J. Piechocki, and K. Chetty, "Using RF transmissions from IoT devices for occupancy detection and activity recognition," IEEE Sensors Journal, vol. 22, no. 3, pp. 2484-2495, 2021, doi: https://doi.org/10.1109/JSEN.2021.3134895
A. K. Kalusivalingam, A. Sharma, N. Patel, and V. Singh, "Employing Random Forests and Long Short-Term Memory Networks for Enhanced Predictive Modeling of Disease Progression," International Journal of AI and ML, vol. 2, no. 3, 2021
B. Barnes-Cook and T. O'Shea, "Scalable wireless anomaly detection with generative-LSTMs on RF post-detection metadata," in 2022 IEEE Wireless Communications and Networking Conference (WCNC), Austin, TX, USA, 2022: IEEE, pp. 483-488, doi: https://doi.org/10.1109/WCNC51071.2022.9771754
N. Varshney, P. Madan, A. Shrivastava, A. P. Srivastava, C. P. KUMAR, and K. Khan, "Real-Time Anomaly Detection in IoT Healthcare Devices With LSTM," in 2023 International Conference on Artificial Intelligence for Innovations in Healthcare Industries (ICAIIHI), Raipur, India, 2023, vol. 1: IEEE, pp. 1-6, doi: https://doi.org/10.1109/ICAIIHI57871.2023.10489823
I. A. Kandhro et al., "Detection of real-time malicious intrusions and attacks in IoT empowered cybersecurity infrastructures," IEEE Access, vol. 11, pp. 9136-9148, 2023, doi: https://doi.org/10.1109/ACCESS.2023.3238664
F. Sattari, A. H. Farooqi, Z. Qadir, B. Raza, H. Nazari, and M. Almutiry, "A hybrid deep learning approach for bottleneck detection in IoT," IEEE Access, vol. 10, pp. 77039-77053, 2022, doi: https://doi.org/10.1109/ACCESS.2022.3188635
M. K. Saeed, A. Al Mazroa, B. M. Alghamdi, F. S. Alallah, A. Alshareef, and A. Mahmud, "Predictive analytics of complex healthcare systems using deep learning based disease diagnosis model," Scientific Reports, vol. 14, p. 27497, 2024, doi: https://doi.org/10.1038/s41598-024-78015-z
M. Al Razib, D. Javeed, M. T. Khan, R. Alkanhel, and M. S. A. Muthanna, "Cyber threats detection in smart environments using SDN-enabled DNN-LSTM hybrid framework," IEEE Access, vol. 10, pp. 53015-53026, 2022, doi: https://doi.org/10.1109/ACCESS.2022.3172304
N. Sun et al., "Cyber threat intelligence mining for proactive cybersecurity defense: a survey and new perspectives," IEEE Communications Surveys & Tutorials, vol. 25, no. 3, pp. 1748-1774, 2023, doi: https://doi.org/10.1109/COMST.2023.3273282
S. Ali, S. U. Rehman, A. Imran, G. Adeem, Z. Iqbal, and K.-I. Kim, "Comparative evaluation of ai-based techniques for zero-day attacks detection," Electronics, vol. 11, no. 23, p. 3934, 2022, doi: https://doi.org/10.3390/electronics11233934
W. Ding and H. Sun, "Prediction of PM2. 5 concentration based on the weighted RF-LSTM model," Earth Science Informatics, vol. 16, pp. 3023-3037, 2023, doi: https://doi.org/10.1007/s12145-023-01111-7
M. Almehdhar et al., "Deep learning in the fast lane: A survey on advanced intrusion detection systems for intelligent vehicle networks," IEEE Open Journal of Vehicular Technology, vol. 5, pp. 869-906, 2024, doi: https://doi.org/10.1109/OJVT.2024.3422253
F. Zahra, N. Jhanjhi, N. Khan, S. N. Brohi, M. Masud, and S. Aljahdali, "Protocol-specific and sensor network-inherited attack detection in IoT using machine learning," Applied Sciences, vol. 12, no. 22, p. 11598, 2022, doi: https://doi.org/10.3390/app122211598