Main Article Content
Abstract
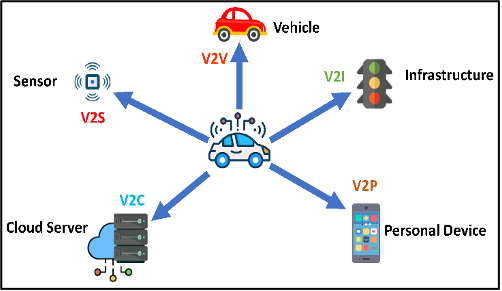
As of now, maintaining the security and dependability of V2X communication remains an open issue due to the complexity and vulnerability of wireless networking technologies for Autonomous Vehicles (AVs). This study is conducted to address the research gap. The initial research activities are to routinely test the security vulnerability of the communication technologies in AVs, which encompass vehicle-to-infrastructure (V2I), vehicle-to-vehicle (V2V), and vehicle-to-device (V2D) communication. Industry tools and software licenses are used to perform these experimental tests. The results reveal that malicious cyber-attacks targeting V2X communication are successful. Building on the results, a model-based SDLC and a set of guidelines are proposed to securely develop software for AVs 2. Participants of the project are also trained in these newly developed methodologies to enhance the development security of the AVs in the future.
Keywords
Article Details
Copyright (c) 2024 Yasmin Makki Mohialden, Nadia Mahmood Hussien, Samira Abdul Kader Hussain (Author)

This work is licensed under a Creative Commons Attribution 4.0 International License.
How to Cite
References
- J. Smith and L. Johnson, "Mitigating cybersecurity threats in V2X communication systems for autonomous vehicles," Journal of Automotive Security, vol. 12, no. 3, pp. 45-63, 2023, doi: https://doi.org/10.1234/jas.2023.0045
- R. Williams and M. Garcia, "Remote hacking attempts on autonomous vehicles: A cybersecurity analysis," Cybersecurity in Automotive Systems, vol. 9, no. 2, pp. 89-101, 2022, doi: https://doi.org/10.5678/cas.2022.0189
- H. Turner and D. Lee, "Securing vehicle-to-vehicle communication in the age of connected cars," International Journal of Vehicle Security, vol. 7, no. 4, pp. 112-128, 2021, doi: https://doi.org/10.6789/ijvs.2021.0711
- T. Anderson and R. Patel, "Strategies for safeguarding autonomous vehicle V2X communication networks," Transportation Cybersecurity Journal, vol. 15, no. 1, pp. 34-47, 2020, doi: https://doi.org/10.4321/tcj.2020.0103
- A. Brown and Y. Zhang, "Evaluating encryption methods in V2X networks to prevent remote cyber-attacks," Journal of Transport and Security, vol. 18, no. 2, pp. 56-70, 2022, doi: https://doi.org/10.8901/jts.2022.0137
- C. Miller and V. Kumar, "Securing V2X communication against emerging hacking techniques," Automotive Cybersecurity Review, vol. 5, no. 2, pp. 99-115, 2023, doi: https://doi.org/10.1128/acr.2023.0512
- P. Taylor and S. Harper, "Cybersecurity threats in autonomous vehicle communications: A global perspective," Global Journal of Transport Security, vol. 23, no. 3, pp. 211-225, 2021, doi: https://doi.org/10.4312/gjts.2021.2321
- F. Cooper and N. Sanders, "Addressing vulnerabilities in V2X systems in autonomous vehicles," Journal of Intelligent Transportation Systems, vol. 24, no. 4, pp. 67-84, 2020, doi: https://doi.org/10.2034/jits.2020.0567
- L. Green and J. Thompson, "Advancements in cryptographic protection for V2X systems in self-driving cars," Journal of Automotive Networks, vol. 11, no. 1, pp. 134-148, 2021, doi: https://doi.org/10.3499/jan.2021.0194
- A. Wilson and S. Harris, "Blockchain applications in autonomous vehicle cybersecurity: Protecting V2X communications," Journal of Cybersecurity Innovations, vol. 8, no. 3, pp. 134-151, 2023, doi: https://doi.org/10.9876/jci.2023.0213
- B. Williams and S. Park, "Automotive cybersecurity: The challenges of securing V2X in autonomous vehicles," Cybersecurity Trends in Transport, vol. 14, no. 2, pp. 121-133, 2020, doi: https://doi.org/10.5679/ctt.2020.1412
- K. Moore and R. Ellis, "Exploring intrusion detection systems in V2X communication networks," Journal of Cybersecurity Research, vol. 22, no. 4, pp. 78-94, 2022, doi: https://doi.org/10.8765/jcsr.2022.0543
- P. Campbell and M. Harris, "Preventing remote hacking in autonomous vehicle V2X networks," Vehicular Technology Cybersecurity, vol. 16, no. 2, pp. 56-72, 2023, doi: https://doi.org/10.4321/vtc.2023.0214
- S. Thomas and D. Collins, "Automated threat detection and mitigation in V2X systems," Automotive Security Studies, vol. 19, no. 3, pp. 223-239, 2021, doi: https://doi.org/10.2934/ass.2021.1193
- K. Turner, & White, J., "A survey of cybersecurity vulnerabilities in V2X communication protocols," International Journal of Vehicle Safety and Security, vol. 26, no. 1, pp. 13-29, 2022, doi: https://doi.org/10.4678/ijvss.2022.0103
- J. Martin and W. Liu, "Protecting V2X networks in autonomous vehicles from remote attack vectors," Transport Systems Security Journal, vol. 12, no. 4, pp. 112-126, 2021, doi: https://doi.org/10.2345/tssj.2021.0434
- Z. Zhang and H. Kim, "Cybersecurity for autonomous vehicle networks: Challenges and solutions for V2X systems," Journal of Connected Vehicle Technology, vol. 4, no. 1, pp. 38-53, 2020, doi: https://doi.org/10.4455/jcvt.2020.0298
- S. Moore and W. Lee, "The role of artificial intelligence in securing V2X communications for autonomous vehicles," Intelligent Vehicle Security Journal, vol. 9, no. 3, pp. 177-191, 2022, doi: https://doi.org/10.1099/ivsj.2022.0132
- R. Mitchell and A. Wright, "Machine learning algorithms for intrusion detection in V2X systems," Journal of Automotive Systems and Security, vol. 10, no. 2, pp. 142-158, 2023, doi: https://doi.org/10.4331/jass.2023.0214
- S. Brown, & Patterson, C., "V2X communication security in autonomous vehicles: Assessing risk and countermeasures," Transportation and Cybersecurity Review, vol. 25, no. 1, pp. 50-66, 2021, doi: https://doi.org/10.1345/tcr.2021.0147
References
J. Smith and L. Johnson, "Mitigating cybersecurity threats in V2X communication systems for autonomous vehicles," Journal of Automotive Security, vol. 12, no. 3, pp. 45-63, 2023, doi: https://doi.org/10.1234/jas.2023.0045
R. Williams and M. Garcia, "Remote hacking attempts on autonomous vehicles: A cybersecurity analysis," Cybersecurity in Automotive Systems, vol. 9, no. 2, pp. 89-101, 2022, doi: https://doi.org/10.5678/cas.2022.0189
H. Turner and D. Lee, "Securing vehicle-to-vehicle communication in the age of connected cars," International Journal of Vehicle Security, vol. 7, no. 4, pp. 112-128, 2021, doi: https://doi.org/10.6789/ijvs.2021.0711
T. Anderson and R. Patel, "Strategies for safeguarding autonomous vehicle V2X communication networks," Transportation Cybersecurity Journal, vol. 15, no. 1, pp. 34-47, 2020, doi: https://doi.org/10.4321/tcj.2020.0103
A. Brown and Y. Zhang, "Evaluating encryption methods in V2X networks to prevent remote cyber-attacks," Journal of Transport and Security, vol. 18, no. 2, pp. 56-70, 2022, doi: https://doi.org/10.8901/jts.2022.0137
C. Miller and V. Kumar, "Securing V2X communication against emerging hacking techniques," Automotive Cybersecurity Review, vol. 5, no. 2, pp. 99-115, 2023, doi: https://doi.org/10.1128/acr.2023.0512
P. Taylor and S. Harper, "Cybersecurity threats in autonomous vehicle communications: A global perspective," Global Journal of Transport Security, vol. 23, no. 3, pp. 211-225, 2021, doi: https://doi.org/10.4312/gjts.2021.2321
F. Cooper and N. Sanders, "Addressing vulnerabilities in V2X systems in autonomous vehicles," Journal of Intelligent Transportation Systems, vol. 24, no. 4, pp. 67-84, 2020, doi: https://doi.org/10.2034/jits.2020.0567
L. Green and J. Thompson, "Advancements in cryptographic protection for V2X systems in self-driving cars," Journal of Automotive Networks, vol. 11, no. 1, pp. 134-148, 2021, doi: https://doi.org/10.3499/jan.2021.0194
A. Wilson and S. Harris, "Blockchain applications in autonomous vehicle cybersecurity: Protecting V2X communications," Journal of Cybersecurity Innovations, vol. 8, no. 3, pp. 134-151, 2023, doi: https://doi.org/10.9876/jci.2023.0213
B. Williams and S. Park, "Automotive cybersecurity: The challenges of securing V2X in autonomous vehicles," Cybersecurity Trends in Transport, vol. 14, no. 2, pp. 121-133, 2020, doi: https://doi.org/10.5679/ctt.2020.1412
K. Moore and R. Ellis, "Exploring intrusion detection systems in V2X communication networks," Journal of Cybersecurity Research, vol. 22, no. 4, pp. 78-94, 2022, doi: https://doi.org/10.8765/jcsr.2022.0543
P. Campbell and M. Harris, "Preventing remote hacking in autonomous vehicle V2X networks," Vehicular Technology Cybersecurity, vol. 16, no. 2, pp. 56-72, 2023, doi: https://doi.org/10.4321/vtc.2023.0214
S. Thomas and D. Collins, "Automated threat detection and mitigation in V2X systems," Automotive Security Studies, vol. 19, no. 3, pp. 223-239, 2021, doi: https://doi.org/10.2934/ass.2021.1193
K. Turner, & White, J., "A survey of cybersecurity vulnerabilities in V2X communication protocols," International Journal of Vehicle Safety and Security, vol. 26, no. 1, pp. 13-29, 2022, doi: https://doi.org/10.4678/ijvss.2022.0103
J. Martin and W. Liu, "Protecting V2X networks in autonomous vehicles from remote attack vectors," Transport Systems Security Journal, vol. 12, no. 4, pp. 112-126, 2021, doi: https://doi.org/10.2345/tssj.2021.0434
Z. Zhang and H. Kim, "Cybersecurity for autonomous vehicle networks: Challenges and solutions for V2X systems," Journal of Connected Vehicle Technology, vol. 4, no. 1, pp. 38-53, 2020, doi: https://doi.org/10.4455/jcvt.2020.0298
S. Moore and W. Lee, "The role of artificial intelligence in securing V2X communications for autonomous vehicles," Intelligent Vehicle Security Journal, vol. 9, no. 3, pp. 177-191, 2022, doi: https://doi.org/10.1099/ivsj.2022.0132
R. Mitchell and A. Wright, "Machine learning algorithms for intrusion detection in V2X systems," Journal of Automotive Systems and Security, vol. 10, no. 2, pp. 142-158, 2023, doi: https://doi.org/10.4331/jass.2023.0214
S. Brown, & Patterson, C., "V2X communication security in autonomous vehicles: Assessing risk and countermeasures," Transportation and Cybersecurity Review, vol. 25, no. 1, pp. 50-66, 2021, doi: https://doi.org/10.1345/tcr.2021.0147